The Brittany region is often described as France’s “Cyber Valley”, a unique ecosystem where 160+ companies, the Ministry of Defense, and research centers collaborate within a tight perimeter, with shared events. Among the companies are both global leaders in cybersecurity (e.g., Sekoia.io) and giants with influence in the field (e.g., Airbus, Thales). From these experiences lessons emerge, both historical and extremely pressing, regarding cyber resilience and the implementation of the NIS2 directive.
Between September 15 and 17, 2025, I participated alongside a delegation of representatives from the private, academic, and public sectors at the launch of the Interreg Europe CAMPUS project in Rennes, on behalf of Digital Innovation Zone, where OPTI is a member.
Below, I analyze the influence of technology giants and research institutes in Brittany. Their approach to new security architectures (e.g., Open XDR), data sovereignty, and resilience. We discuss the lessons, each with an actionable conclusion for the reader of this article, and what a proactive approach means in implementing NIS2.
Orange Cyberdefense: OT – IT Convergence at a Global Scale
Orange Cyberdefense is one of the largest global cybersecurity players, with over 18 SOCs and 3,100 experts, with solutions adapted to the global market.
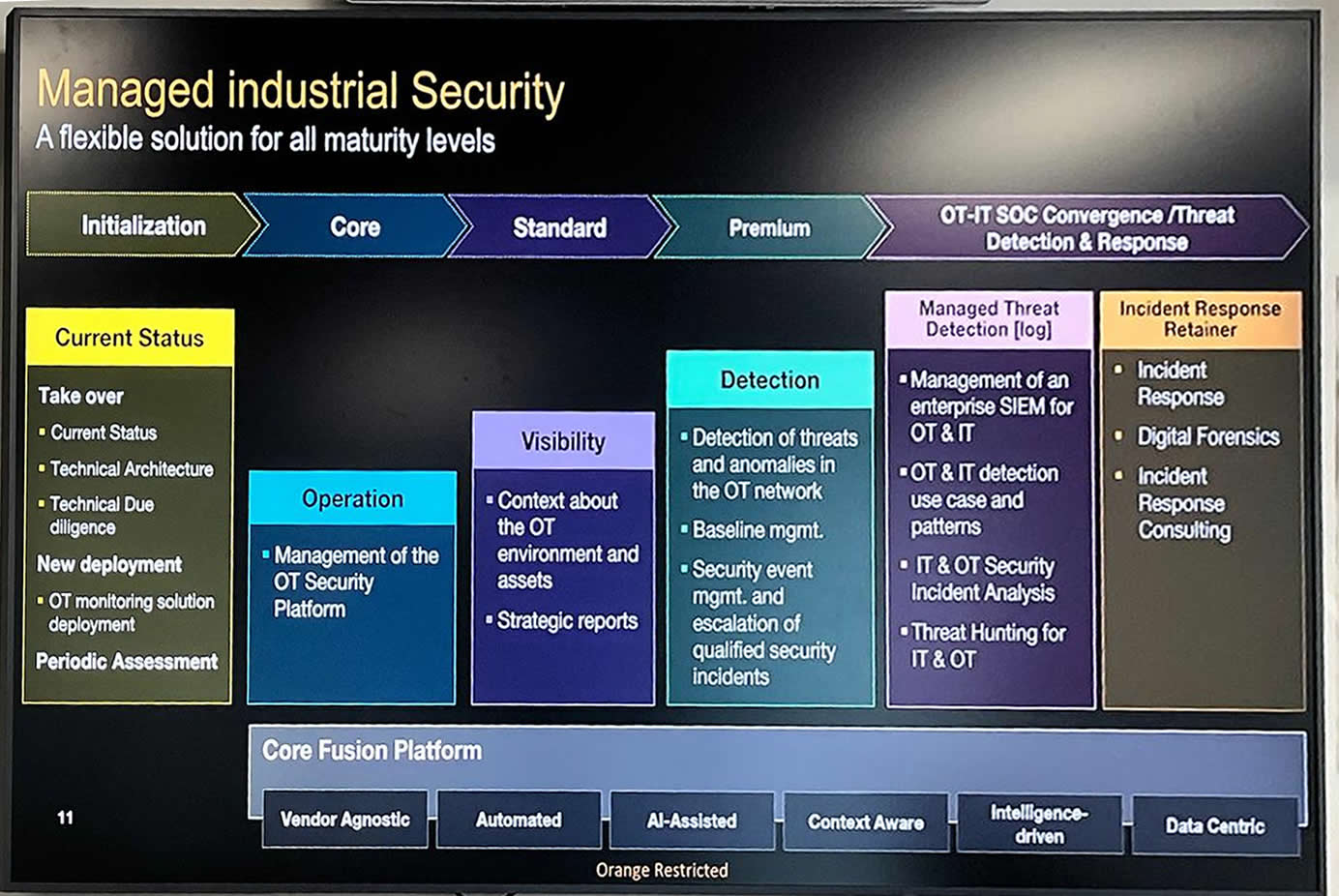
The main challenge raised by industrial or corporate clients is the need for a unified OT (operational technology – industrial equipment) & IT (information technology – office) SOC. What Orange Cyberdefense does is a strict staging of protection toward the goal of total visibility:
- They can cover both OT and IT, but they start from OT toward IT to place operations at the center.
- The implementation phases for industrial security are: Initialization (audit and monitoring), Core (OT security management), Visibility (OT context and reporting), Premium (OT threats), OT-IT Convergence & XDR (SIEM for IT & OT, Incident response) – for details see the photo below. They may sound like commercial names, but they show the fundamental direction of protection.
- A major differentiator is cost-reduction consulting through technology consolidation and calculating TCO (total cost of ownership), together with compliance assistance.
The vast majority of incidents that a large company will encounter will not come from “zero-day” attacks, but from poor cyber hygiene in complex infrastructures and technological misalignment.

What does NIS2 require you to be able to demonstrate (audit)?
NIS2 shifts the emphasis from “checkboxes” to risk management and reporting measures:
- Inventory and dependencies: what assets exist, what systems are critical, what depends on what (including suppliers/supply chain).
- Vulnerability management and patching: how you identify, prioritize, and remediate (or control) exposure.
- Incident handling & reporting: the capability to detect, manage, and report incidents according to requirements.
- Governance and accountability: roles, decisions, evidence, accountability at the management level.
For more, see the cybersecurity page and our guide for AI security.
Sekoia.io and the Shift to Open XDR: Information Dictates Defense
Sekoia.io is a European company that in 2025 is competing with traditional giants such as Splunk or QRadar in many SOCs, some in the U.S., according to the presentation in Rennes. The company is betting on a fundamental paradigm shift, relevant for any CISO or CTO: the move from monolithic SIEM systems to Open XDR (Extended Detection and Response).
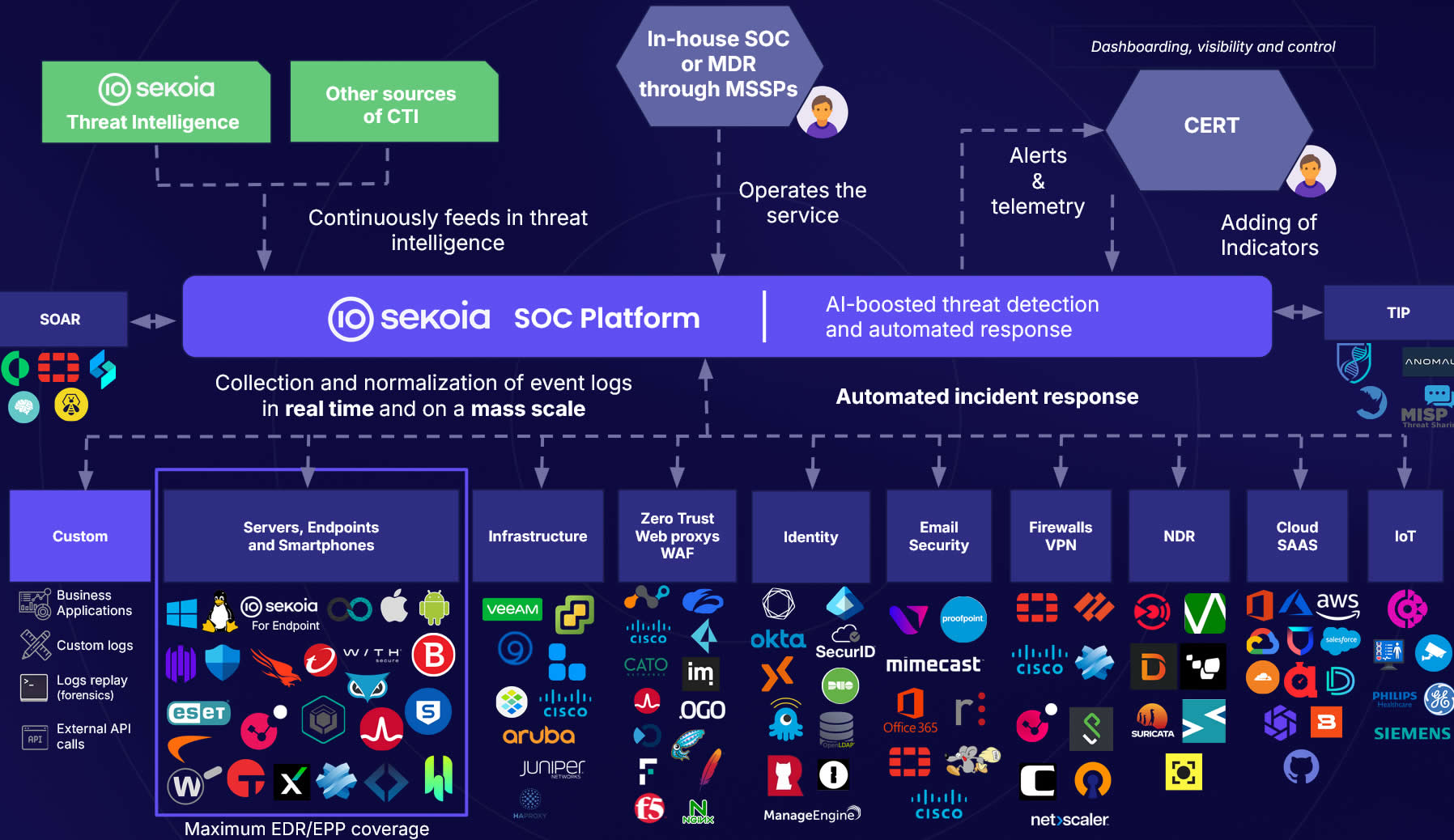
Sekoia.io’s original approach:
- You cannot monitor everything mixed together without priorities. Sekoia built the platform starting from CTI (Cyber Threat Intelligence).
- Instead of collecting only logs and hoping it finds anomalies, the system is continuously fed with information about what attackers look like.
- The principles are: Anticipation and automation (including with AI), Open architecture and interoperability (over 250 third-party tools), Democratization (the open SOC platform, >1000 easy-to-use rules),
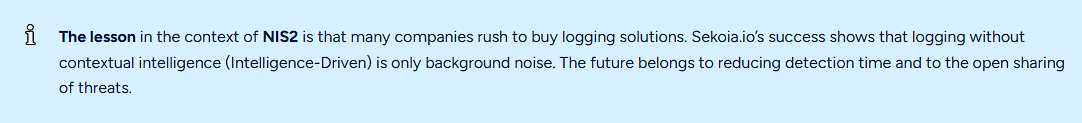
The role of artificial intelligence in cybersecurity:
In cybersecurity, AI brings value when it works over structured data: clean inventory, correlated vulnerabilities, patching history, access. AI can help with prioritization (What matters now?), explanation (Why is a risk critical?), actionable recommendations (What are the next steps?). AI cannot replace inventory, patching discipline, etc., the risk being the so-called “security hallucination.”
Another organization in Rennes is SequoIA (distinct from Sekoia.io), an AI cluster formed by the university and companies, dedicated to the intersection between AI and the defense industry, with a focus on trustworthy and verifiable AI and part of a French AI Factory.
For a hybrid approach to AI, see our Report for AI in B2B 2026 and this guide to RAG.
Inria and “High Security Lab”: Security is Built, not Imported
Inria (the National Institute for Research in Digital Science and Technology) is a research organization with multiple sites in France, where over 2,800 employees (85% scientists) work in formal research for computer science (mathematics, computer science, artificial intelligence), at least 240 of them in cybersecurity. Notably, from Inria came over 200 startups, 75% of them successful (either acquired, or still existing independently), according to the institute’s presentation.
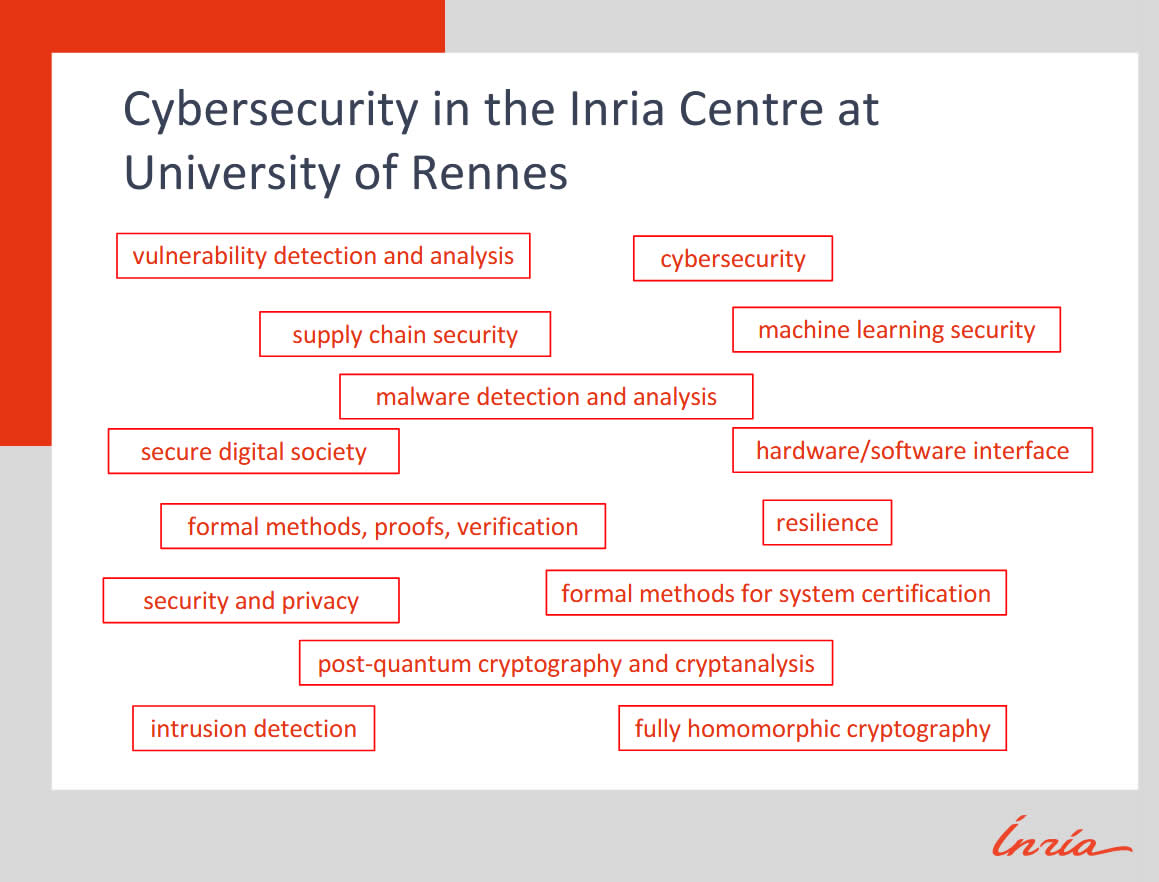
In Rennes, Inria’s research teams are formally studying at this moment both classic domains (Intrusion Detection, Vulnerability Detection and Analysis – collaborating with NIST in the U.S., Malware Detection and Analysis etc) and also some domains that may be food for thought for a company manager or CISO:
- Post-quantum cryptography and cryptanalysis
- The hardware-software interface
- Formal methods for system certification
Thus, Inria’s research covers even the physical hardware level (e.g., side-channel attacks or supply-chain attacks) as well as verifiability, all aspects covered by NIS2. Vulnerabilities can come pre-installed, so you must rigorously audit the security of your equipment suppliers, not only your own network.
CyberSchool and Pôle d’Excellence Cyber: Security as Infrastructure
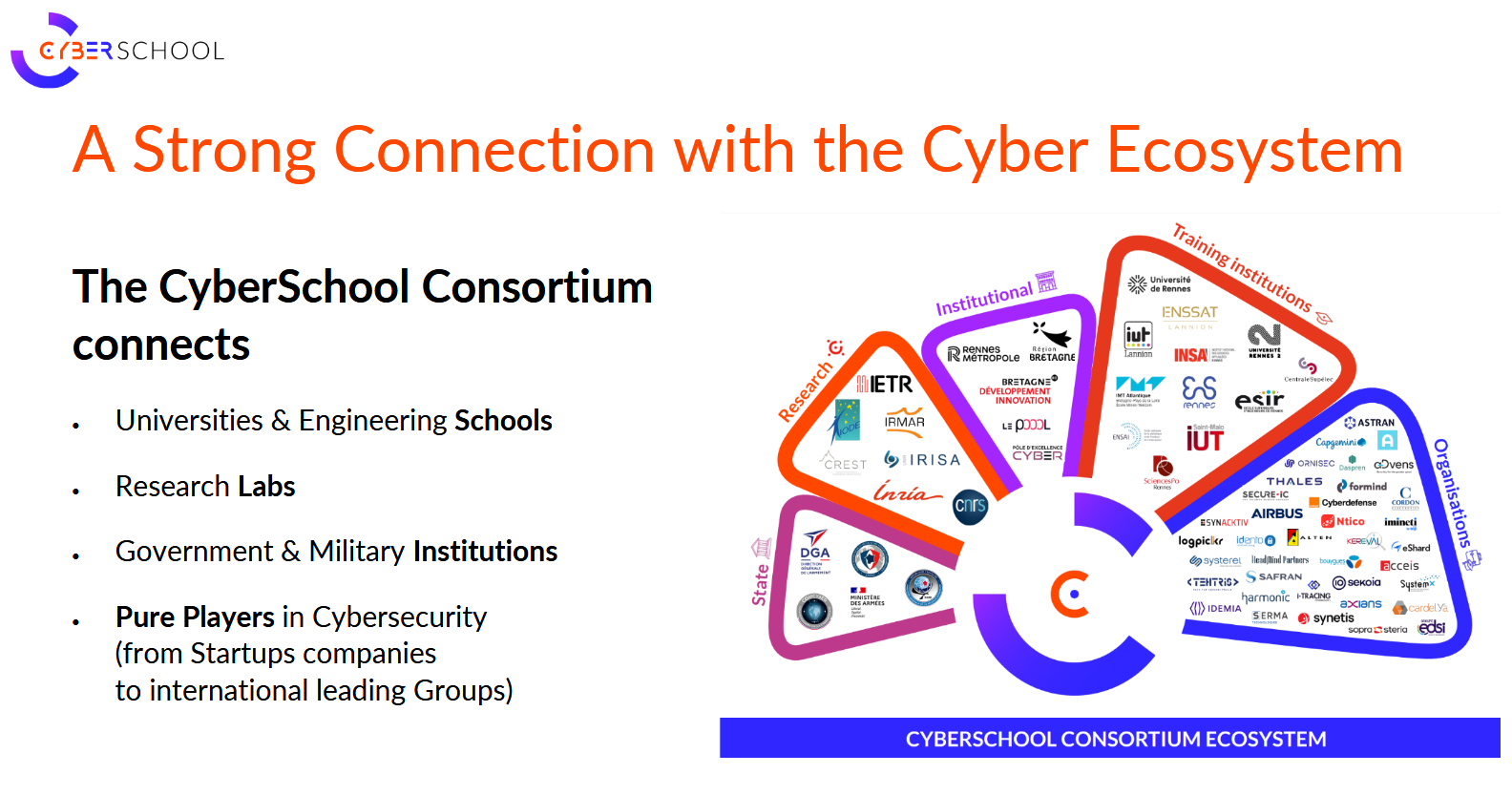
What strikes you in Rennes is the lack of barriers between academia and the private sector. CyberSchool is a consortium that brings together universities, research laboratories, and “Pure Player” companies (such as Airbus, Thales, Orange Cyberdefense). It does not produce only theoreticians.
The 750+ students, some in naval security (given the nearby military ports in Brittany) and 120+ PhD candidates are directly connected to industry needs. And Pôle d’Excellence Cyber was created to strengthen the cybersecurity sector in Rennes through training, academic research, and collaborative innovation.

Visibility before Compliance
As we saw with Orange and Inria, the main effort is in understanding and getting visibility of the infrastructure (“passive security“), compliance being only the documented result of this reality. Therefore, passive security means:
- Maintaining a continuously updated inventory of assets, locations, and networks.
- Understanding vulnerabilities and attacks at the device, location, user, and platform level.
- Monitoring risk over time, not only reacting to incidents.
Then XDR (Extended Detection and Response) is added in an open format. Since the era of monolithic solutions is ending, modern architectures allow rapid integration of various security tools, as we saw as part of Sekoia.io’s success.
Moreover, this is the external validation of the MrBenny.com (public beta) architecture by OPTI, which creates distinct editions ‘Passive Security’ (for inventory and vulnerabilities) and ‘Compliance’ (for task management and risk analysis). You cannot do compliance on an asset you do not know you have.
Proactive vs. Reactive Compliance
Regarding compliance, although France is extremely rigorous with regulations and standards NIS2, GDPR, ISO 27001 (ANSSI being the institution in charge), all organizations of excellence build compliance only secondly, after having operational clarity first.. It is a radical contrast with the reactive implementation of NIS2: audits on paper, written procedures, and the purchase of disparate tools, without knowing exactly what you are protecting.
The difference is not budget, but priorities, as this table shows:
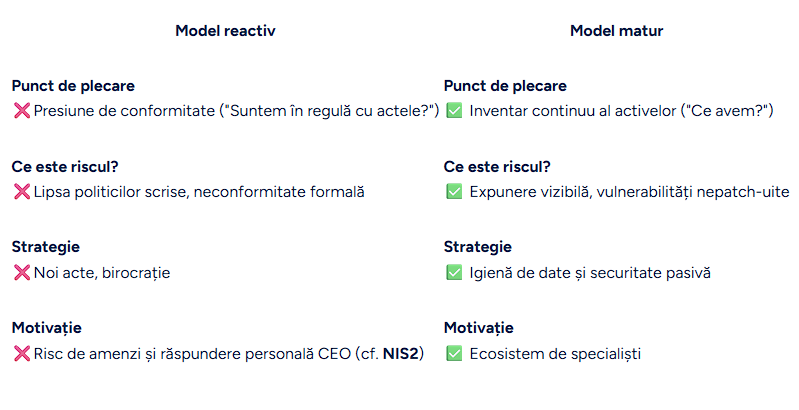
In the Breton ecosystem, the central idea repeats itself. Resilience does not start with the audit, but with operational clarity. If the steps are taken in the correct order described above, NIS2 compliance becomes easy, not a difficult imposition.
At OPTI Software, we integrate these cyber architecture principles both into our business solutions (see details), and into our risk management product, MrBenny.com (public beta).
Article taken from the website: https://www.opti.ro/



